· Sebastian Schrittwieser · Dissemination · 2 min read
Paper accepted at ACM Computing Surveys
Our paper about evaluation methodologies in software protection research has been accepted at ACM Computing Surveys.
We are pleased to announce that our paper, “A Survey on Data-Driven Software Vulnerability Assessment and Prioritization,” has been accepted for publication in ACM Computing Surveys (A*-rated). This work is a collaboration with the University of Gent. The paper is available as Open Access.
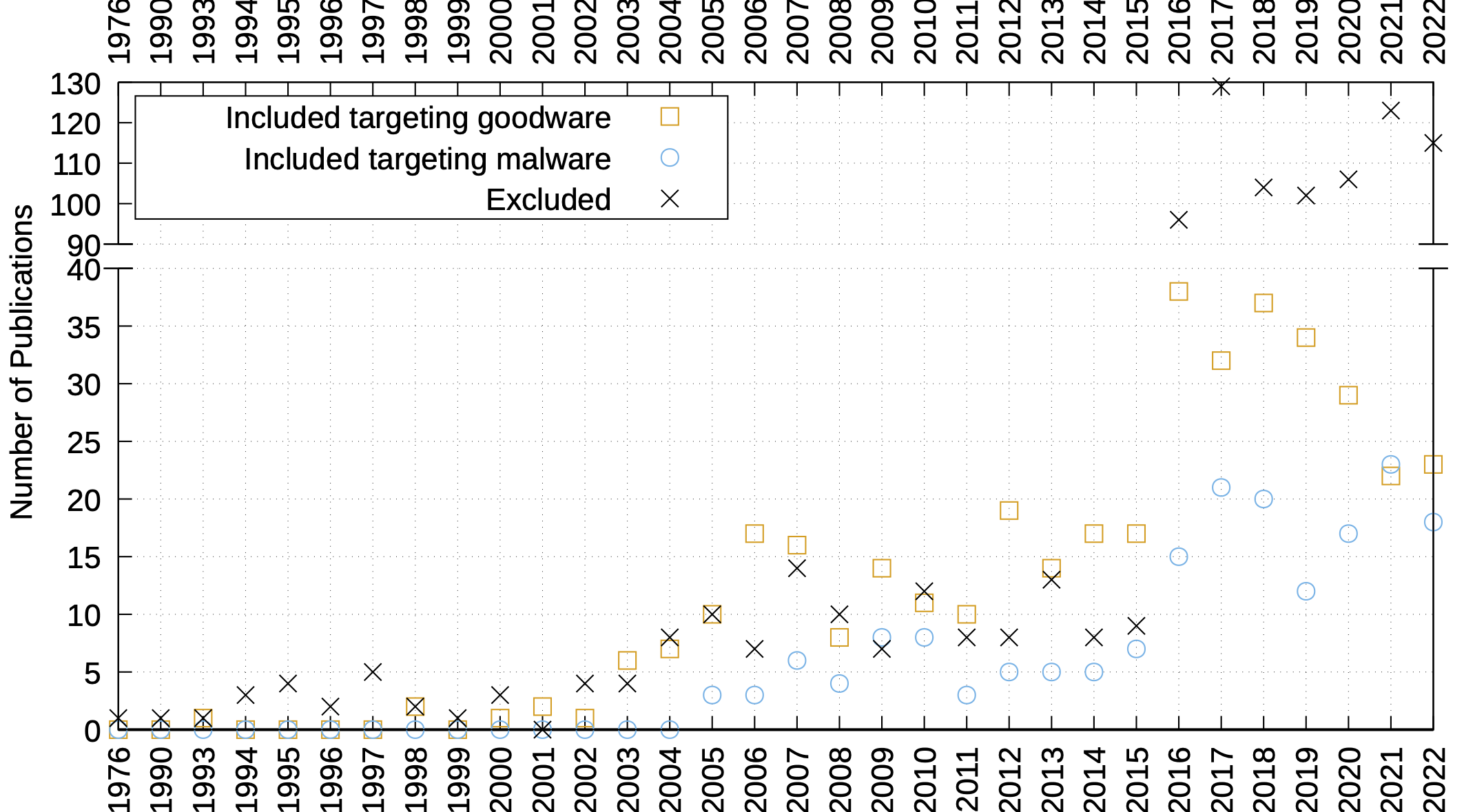
Abstract: Man-at-the-end (MATE) attackers have full control over the system on which the attacked software runs, and try to break the confidentiality or integrity of assets embedded in the software. Both companies and malware authors want to prevent such attacks. This has driven an arms race between attackers and defenders, resulting in a plethora of different protection and analysis methods. However, it remains difficult to measure the strength of protections because MATE attackers can reach their goals in many different ways and a universally accepted evaluation methodology does not exist. This survey systematically reviews the evaluation methodologies of papers on obfuscation, a major class of protections against MATE attacks. For 571 papers, we collected 113 aspects of their evaluation methodologies, ranging from sample set types and sizes, over sample treatment, to performed measurements. We provide detailed insights into how the academic state of the art evaluates both the protections and analyses thereon. In summary, there is a clear need for better evaluation methodologies. We identify nine challenges for software protection evaluations, which represent threats to the validity, reproducibility, and interpretation of research results in the context of MATE attacks and formulate a number of concrete recommendations for improving the evaluations reported in future research papers.